Pattern Discovery¶
Summary¶
DTonomy automatically cross-correlates alerts with DTonomy’s patent-pending advanced correlation/graph mining algorithm and presents them intuitively against the MITRE ATT&CK framework. By augmenting the manual cross-correlation process with AI-based discovery, security teams can analyze significantly more alerts in less time with new insights. Besides reducing analyst efforts, this automation also reduces the risk that alerts requiring attention will go un-investigated.
DTonomy continuously collects feedback from users and provides customer-specific adaptive risk scores based on historic trends. This eliminates time spent repetitively reviewing false positives, enables focus on highest risk issues personalized to your environments, and identifies associated risks sooner. Meanwhile, DTonomy AIR also learns decision patterns from senior security analysts driving continuous knowledge transfer across the team.
Continuous Pattern Discovery¶
As you start ingesting security alerts to the platform and triaging them, our pattern discovery engine are working hard to identify patterns that help you quickly correlate them to meaningful stories or enable you make decision and transfer knowledge easily between team. The embedded algorithms are ranging from graph ML to decision reasoning. We have packaged them up so that you do not need to worry about the results. When it suggests, you can see them marked as Recommend. You can click each pattern and view them.
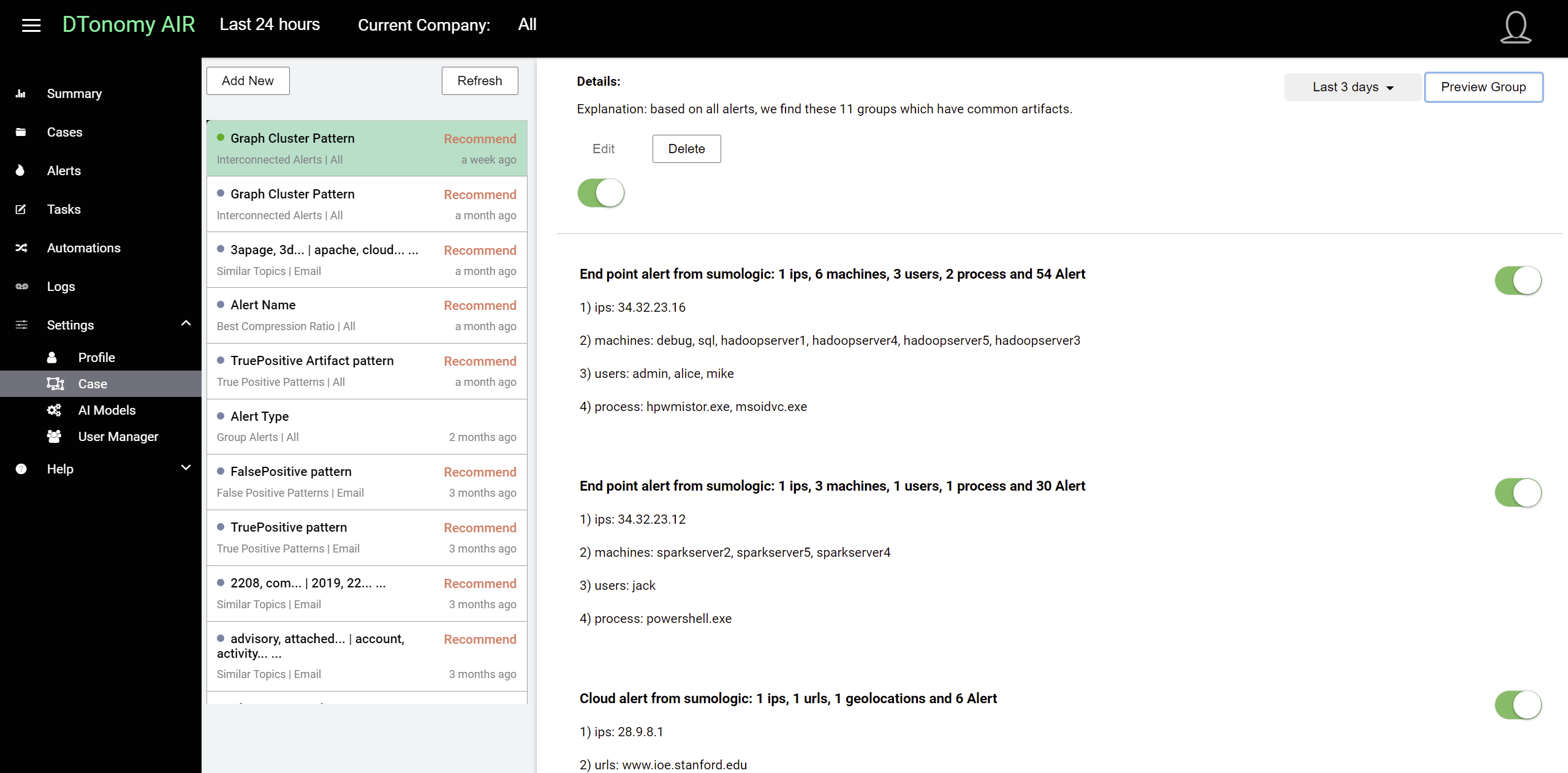
Verify the pattern¶
You can always verify the pattern on your historical data by clicking previewing the patterns on the top right corner.
In this example pattern, you can view the relevant artifacts in each individual group.
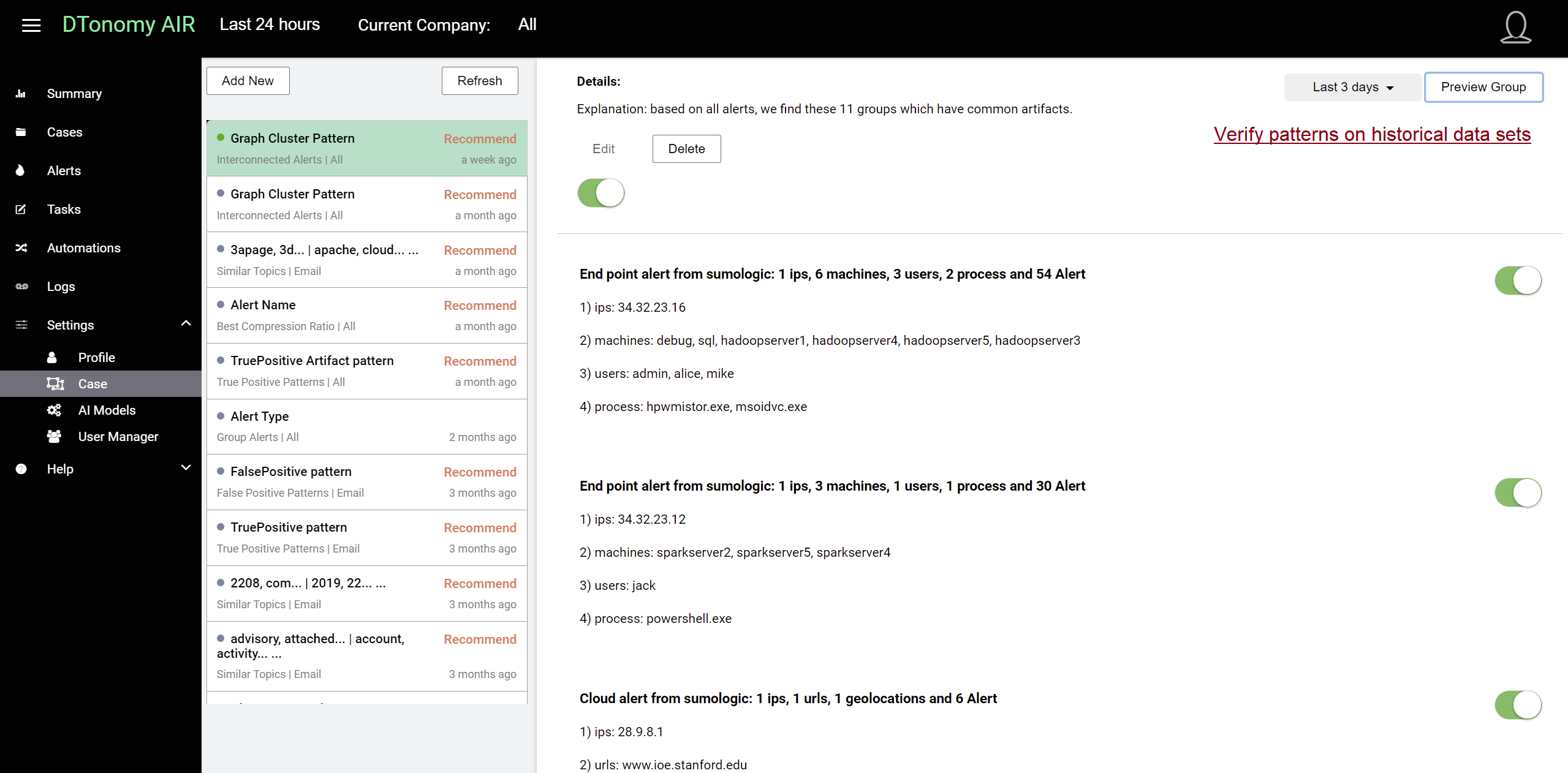
In this example pattern, you can preview sample historical alerts that falls into each individual group.
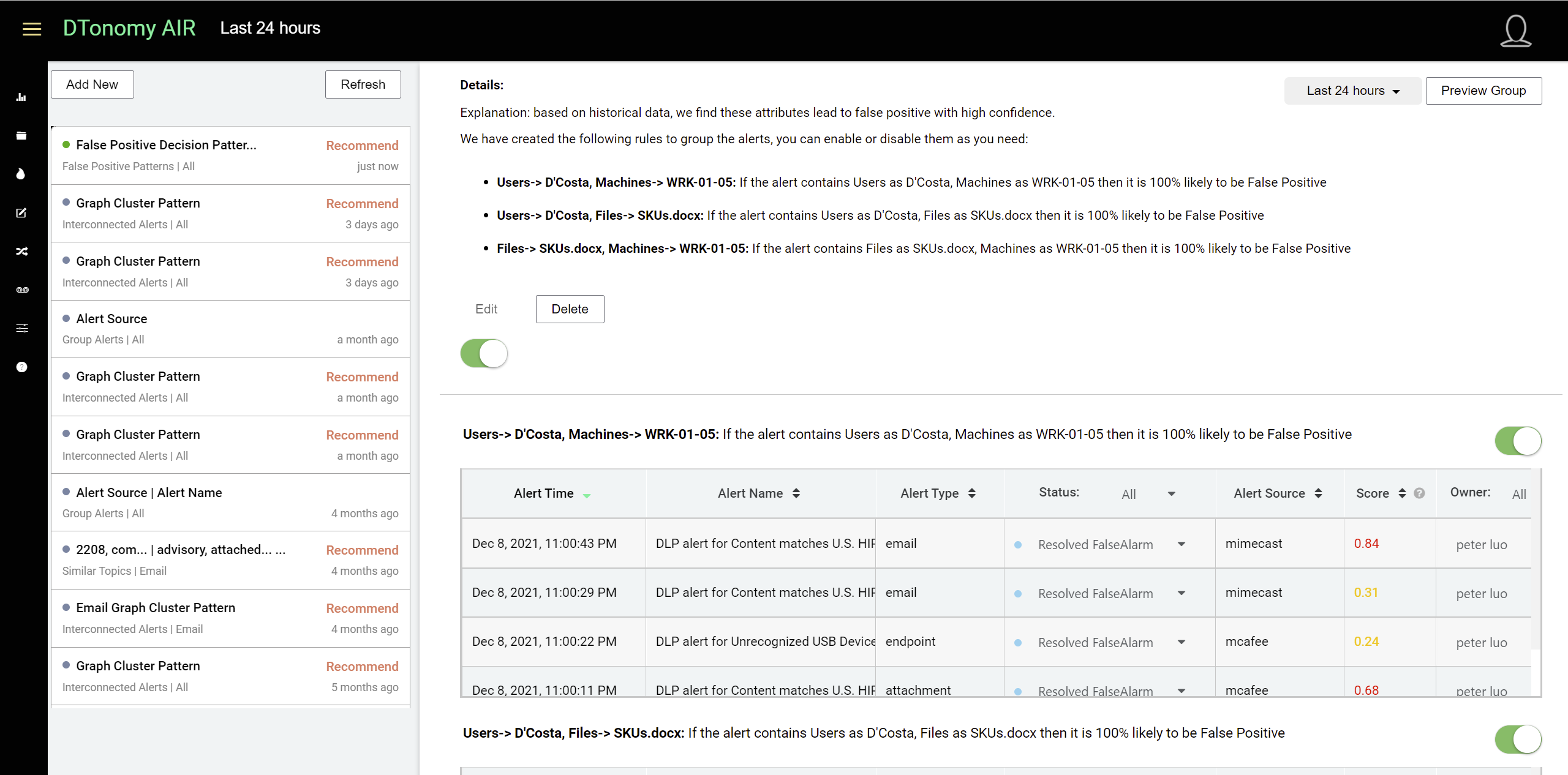
Enable the pattern¶
After viewing the pattern against historical data, you can choose to enable or disable pattern via the toggle. Once pattern is enabled, you can view relevant cases under case page.
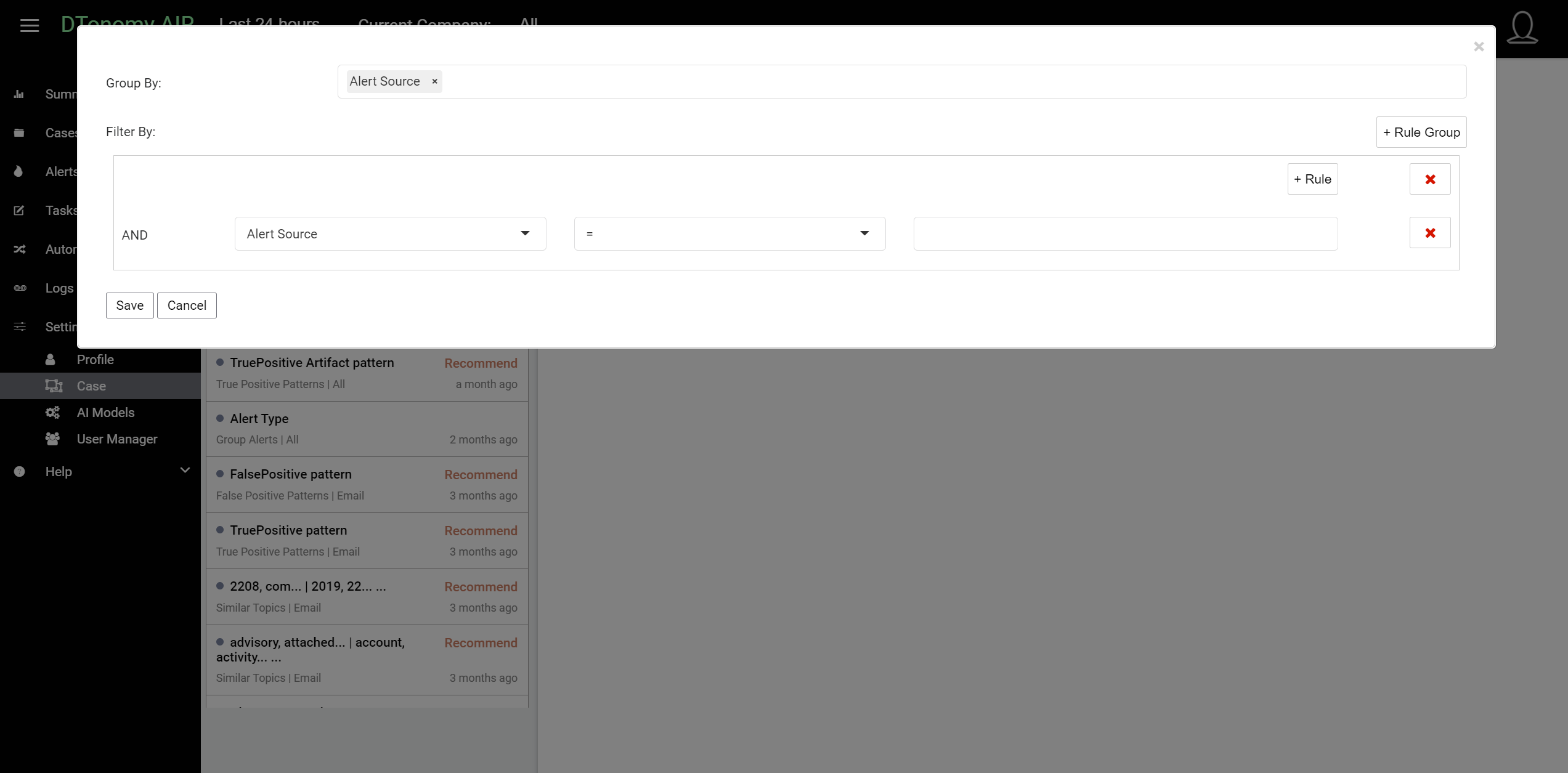
Manual option¶
If you would like to manually suggest the patterns, you can click “Add New” button and start editing your patterns.
View Pattern Based Cases¶
Once pattern is enabled, the incoming alerts will be automatically converted to cases continuously.
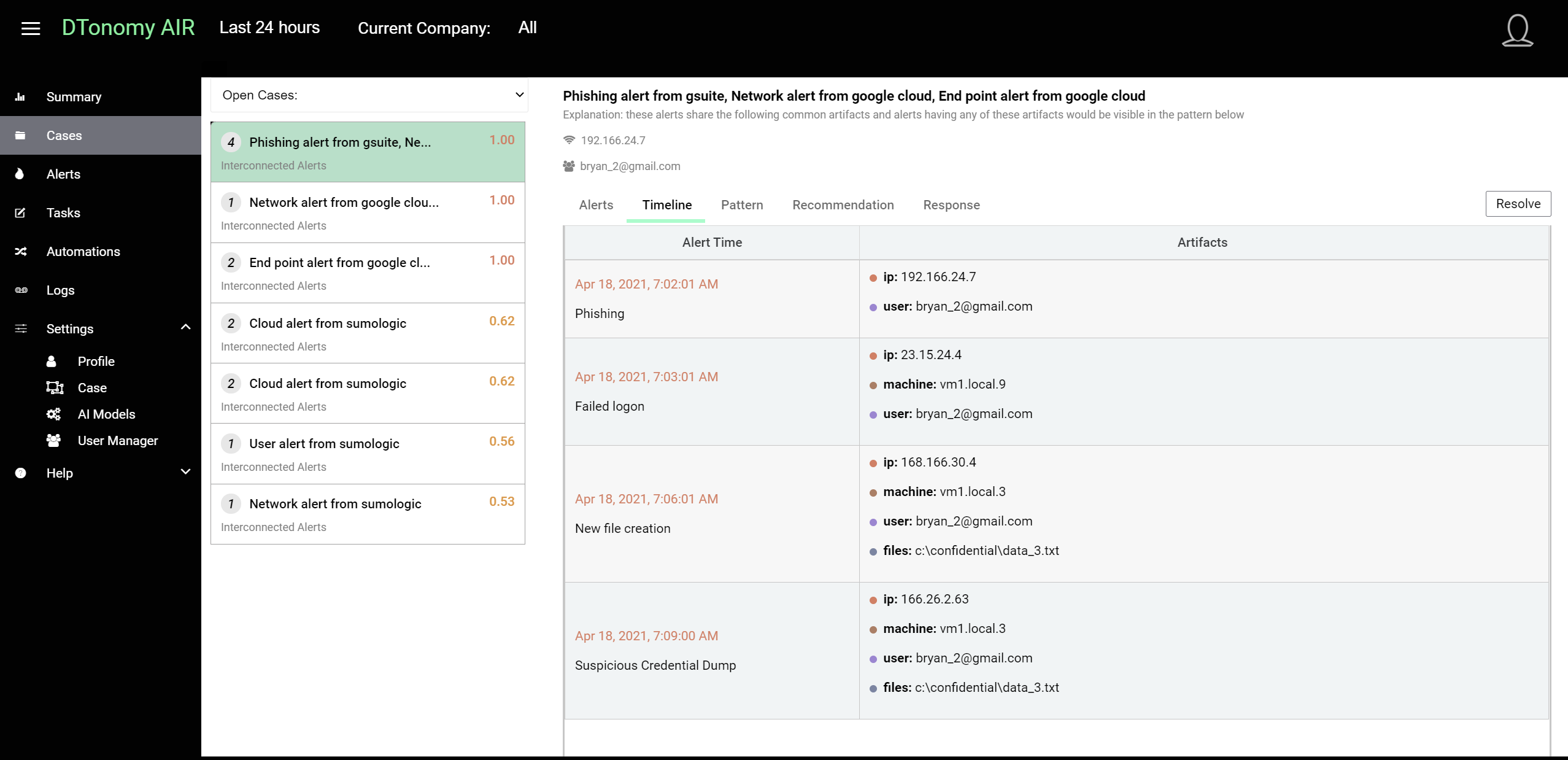
Graph visualization¶
You can view connections between artifacts in graph view. The shared artifacts are in red dots and everything else are expanded connections from shared elements.
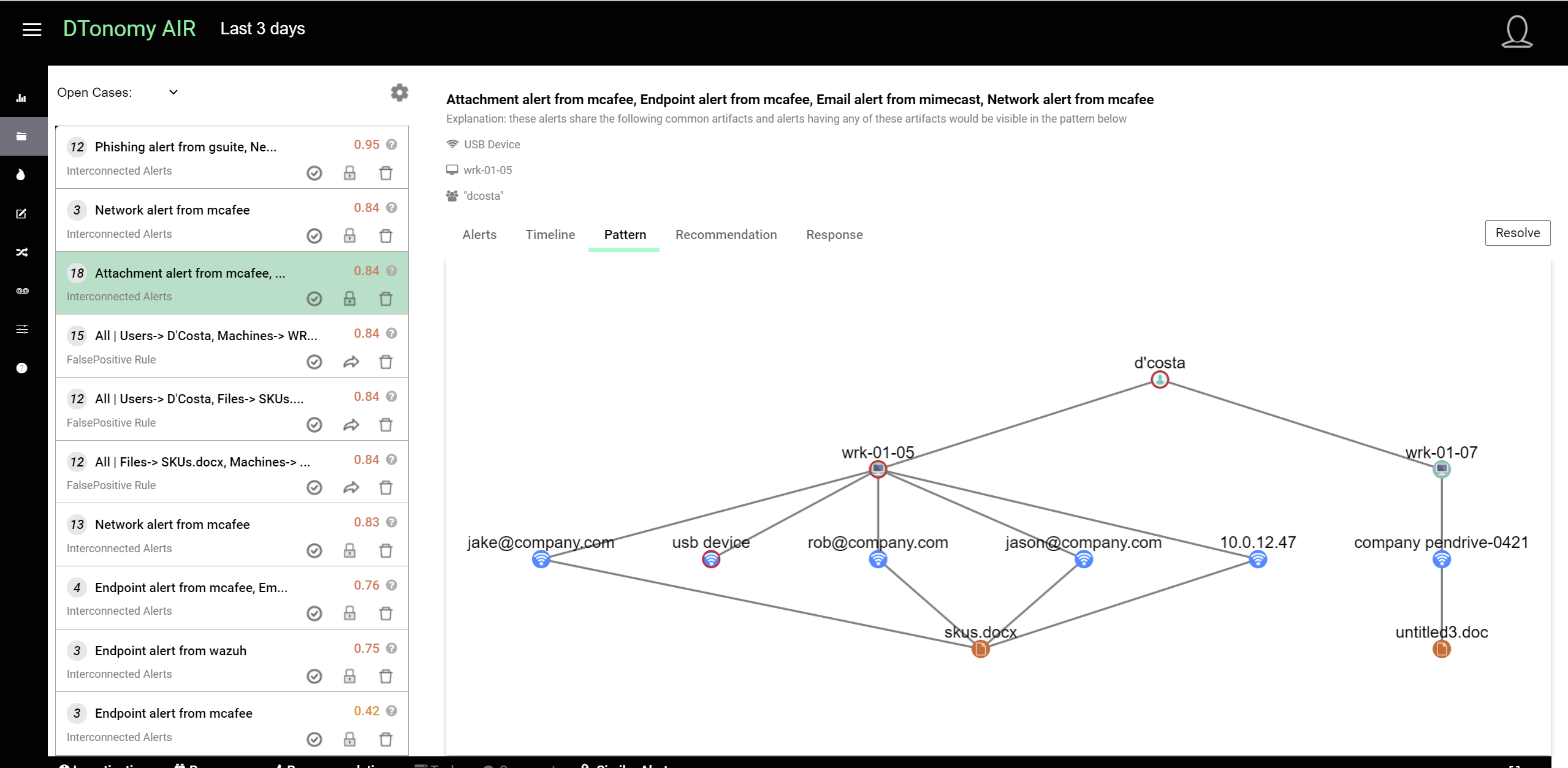
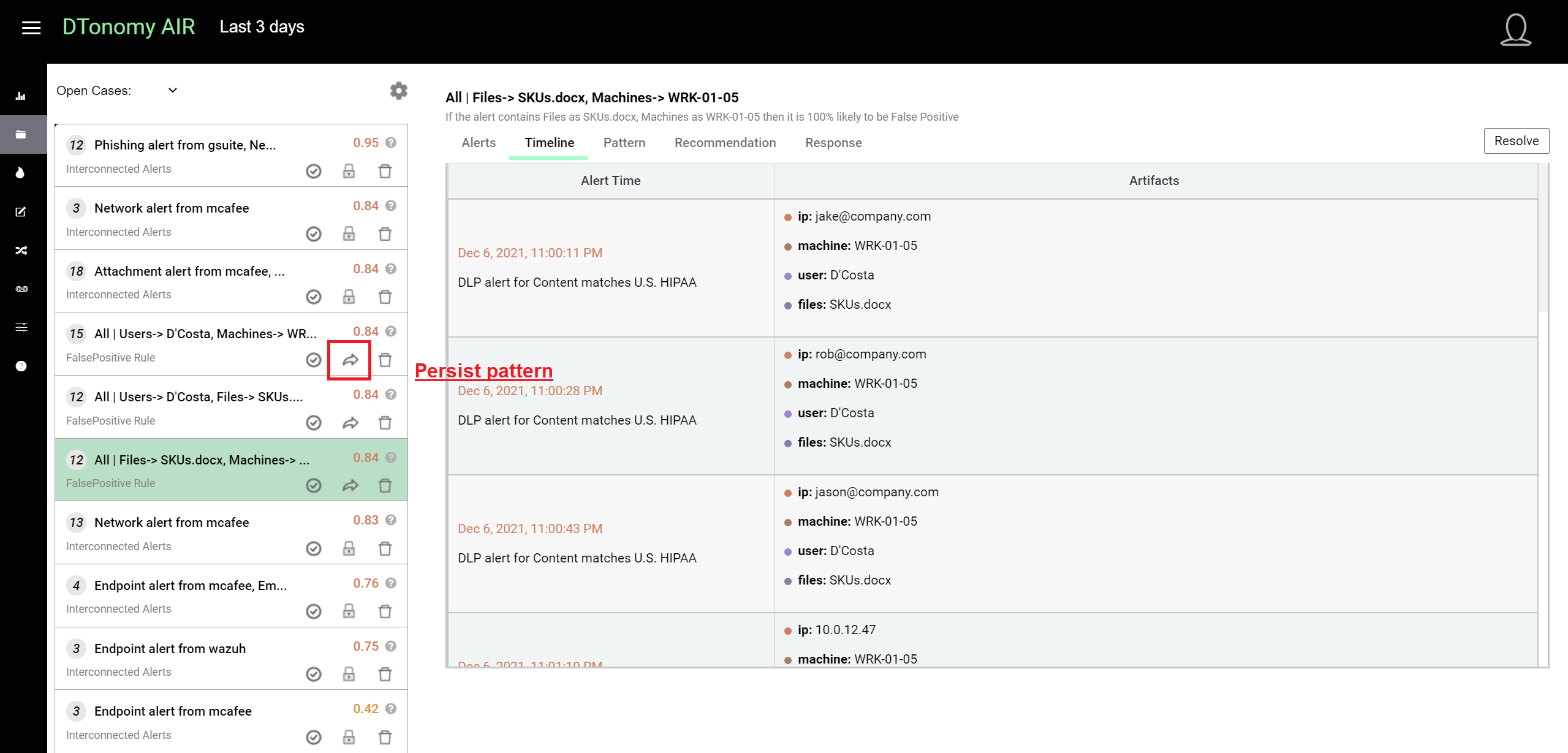
Persist pattern¶
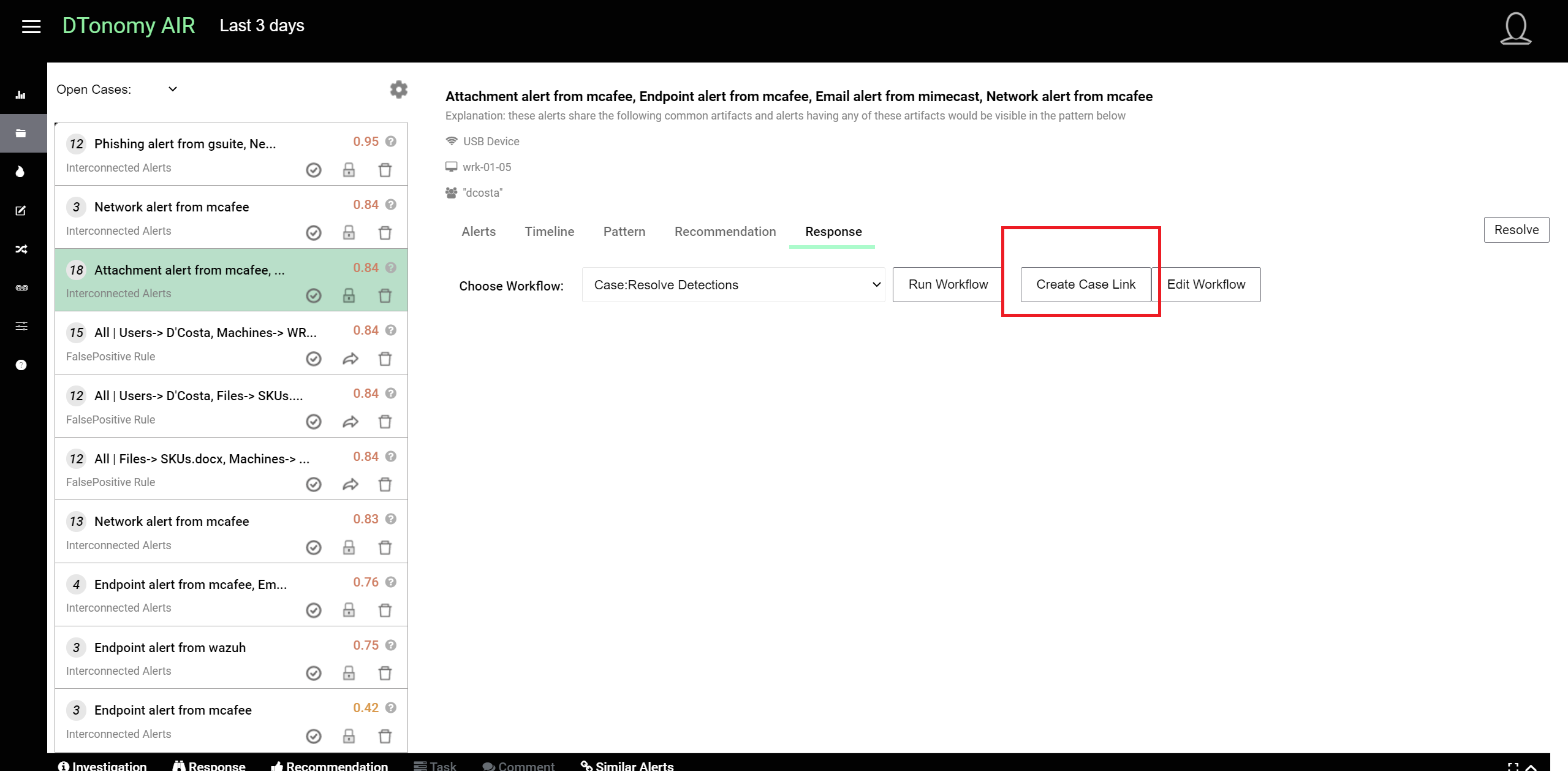
After you review the cases and you feel this case should be persisted for everyone to use, you can click the share icon to persist it in the database. Once it is persisted, your team member will start see the pattern.
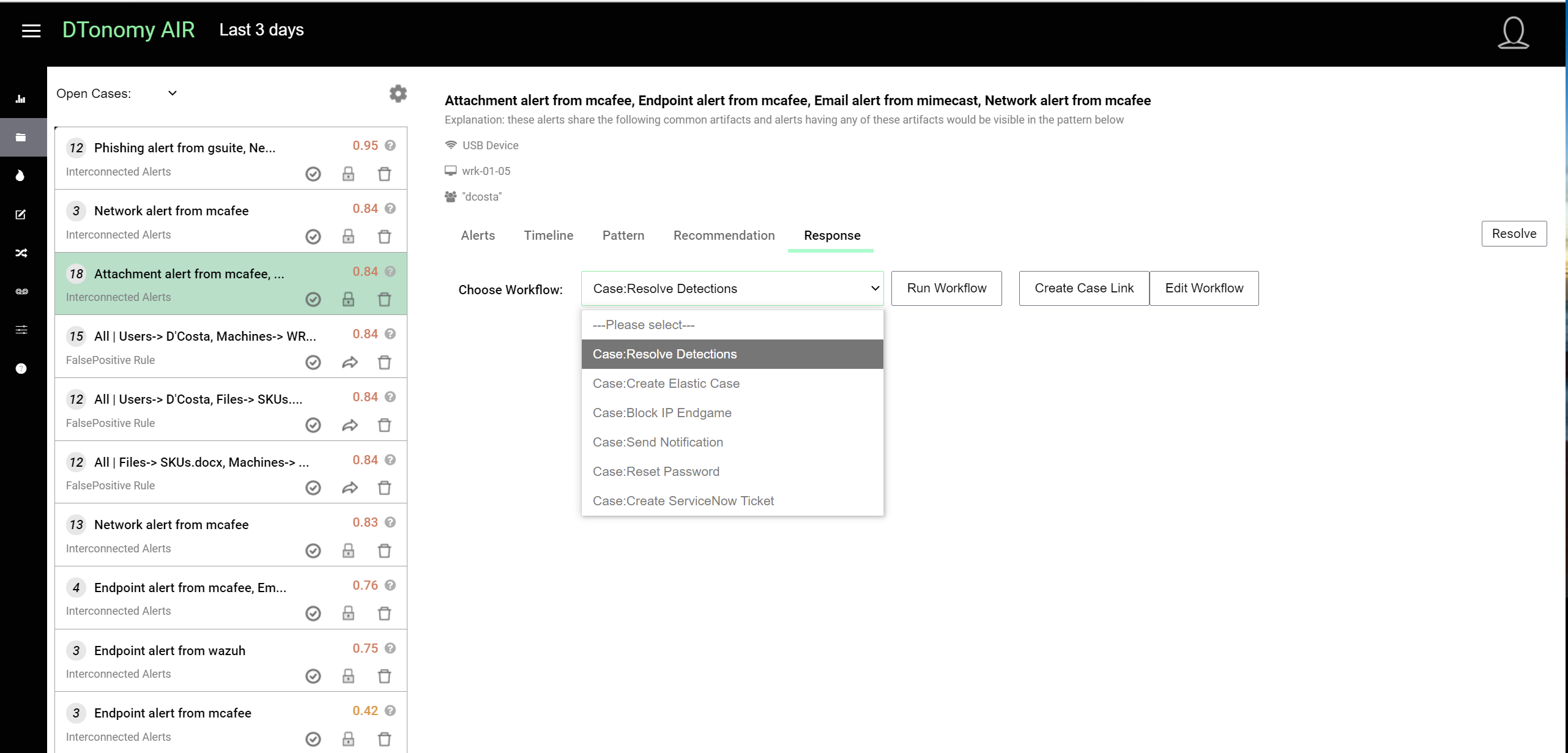
Response to Cases¶
AI Recommendation¶
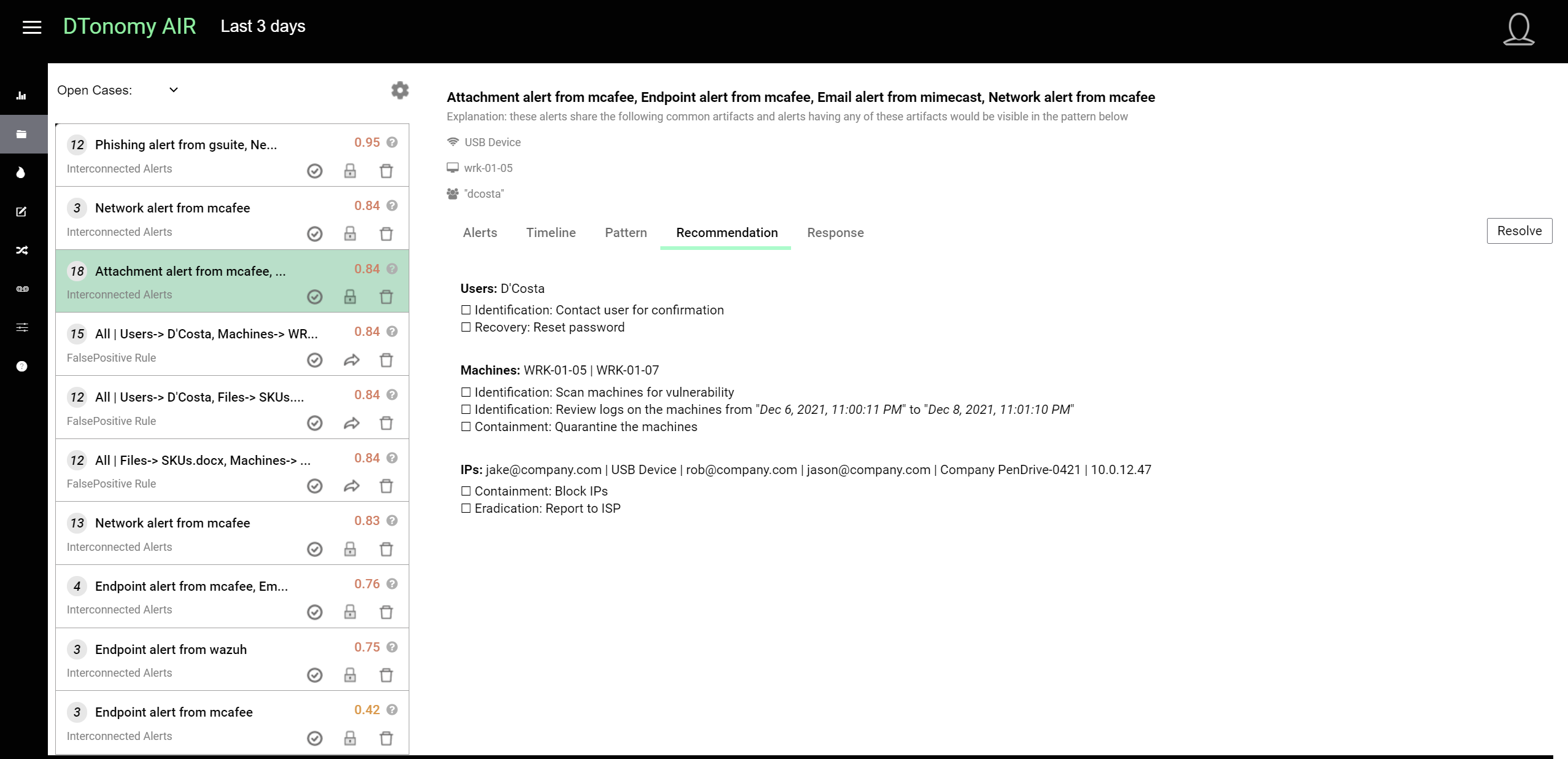
Our AI engine analyzes all the detections you have and provides recommendations on actions you should take.
Batch Resolve¶
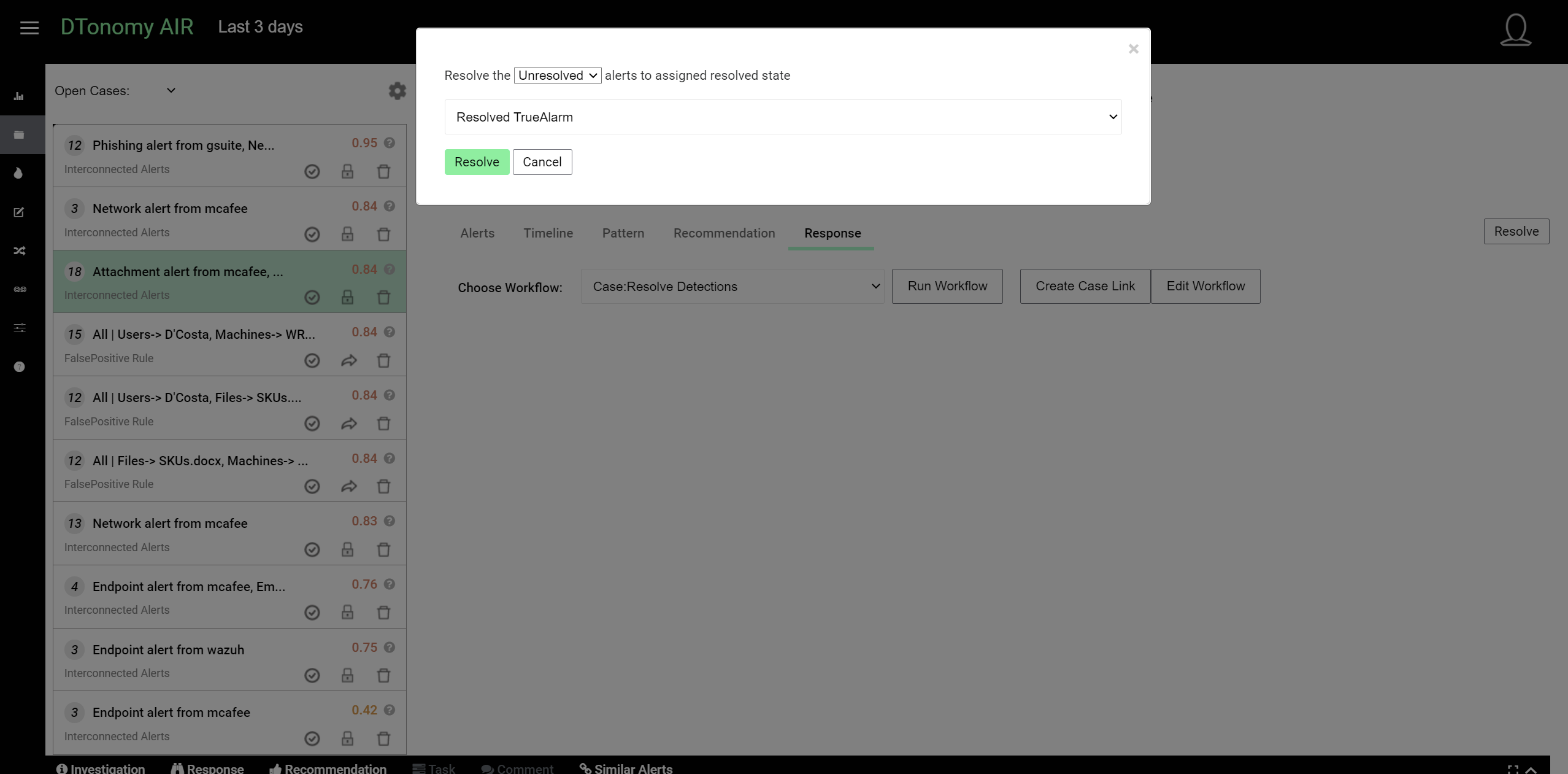
For all the alerts within a case, you can batch resolve them to true positive or false positives. Once all the cases are resolved, they will be moved to resolved cases category. If future alerts fall into the pattern, the case will be waken up.
Response to cases¶
You can create automatons to response to cases via drag and drop workflow.
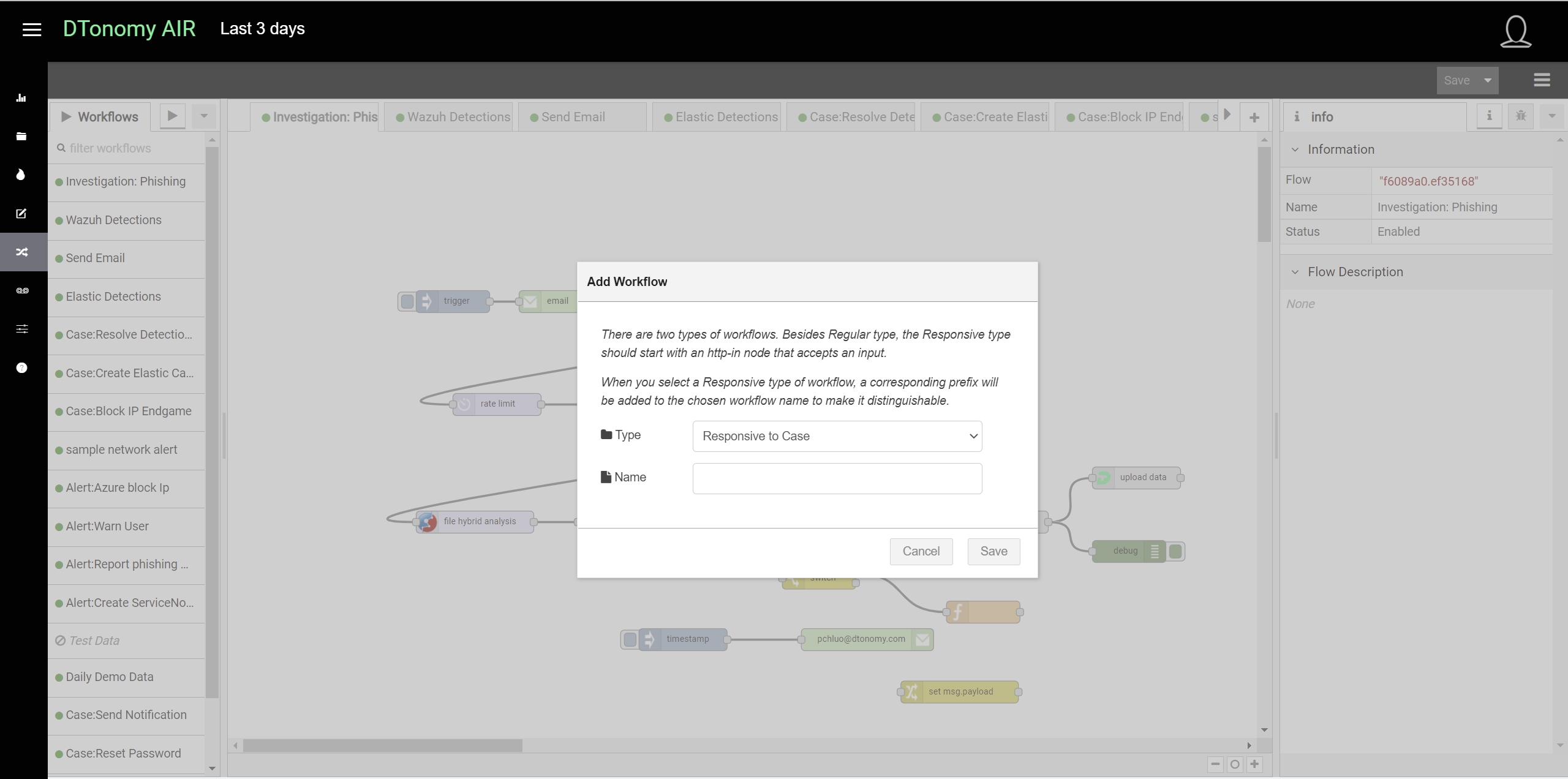
Once an automation is created, you can see them show up in the drop down list.